MDAC 2.5 SDK - Technical Articles
November 1998
By Kamaljit Bath
With millions of people surfing the Internet and downloading vast quantities of information every day, security is now a vital issue. Microsoft recognizes this and has taken precautions to ensure that the information you seek is not only easy to obtain but also arrives safely on your computer.
The goal of security development in Microsoft® Internet Explorer is to ensure that the following conditions are met:
To promote this goal, some ADO and RDS objects have been modified so that they will adhere to security settings in a host environment such as Internet Explorer. Users who access Web sites that contain ADO and RDS applications should adjust their Internet Explorer security settings so that they can access these applications and at the same time protect their computer and data from potentially damaging controls or applications.
This document examines the following features of Internet Explorer 4.0 or later:
Both developers and users of Web applications should understand the security zones, security levels and how to customize the zones when working with ADO and RDS Web applications. Developers should understand the restrictions Internet Explorer places on ADO and RDS objects and the security differences between MDAC 2.0 and 2.1.
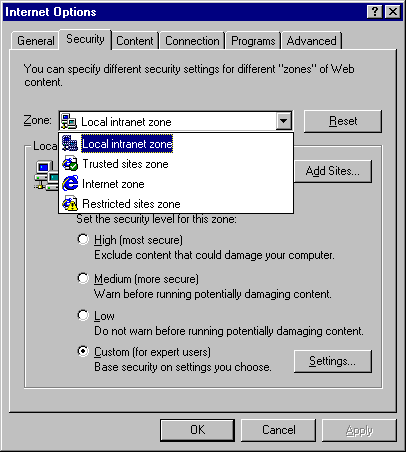
Each of the four zones and it's default security level in Internet Explorer 4.x and 5.0 are described in the following table.
| Zone | Description |
| Local Intranet | Contains Web sites that can be accessed without using a proxy server or a modem. (These are the Web sites on your intranet.) The default security level is Medium in Internet Explorer 4.x. In Internet Explorer 5.0, the default security level is Medium-Low. |
| Trusted Sites | Contains Web sites that you trust—sites that you believe you can download or run files from without worrying about damage to your computer or data. You can assign sites to this zone. The default security level is Low in Internet Explorer 4.x and 5.0. |
| Internet | Contains anything that is not on your computer or an intranet, or assigned to any other zone. The default security level for the Internet zone is Medium in Internet Explorer 4.x and 5.0. |
| Restricted Sites | Contains sites you don't trust—that is, sites that you're not sure whether you can download or run files from without damage to your computer or data. You can assigne sites to this zone. The default security level is High in Internet Explorer 4.x and 5.0. |
For more detailed information about Internet zones, see your Internet Explorer documentation.
For each zone, you can specify a security level. For Internet Explorer 4.x and 5.0, the available security levels are described in the following table.
| Security level | Description |
| High | Excludes content that could damage your computer. |
| Medium | Warns you before running potentially damaging content. |
| Medium-Low | Available only in Internet Explorer 5.0. Does not prompt you each time potentially damaging content appears. Most content will run without prompts, and unsigned ActiveX® controls will not be downloaded to your computer. |
| Low | Does not warn you before running potentially damaging content. |
| Custom | A security setting of your own design. Use this level to customize the behavior of ADO and RDS objects in a specific zone. |
The following illustration shows the four security levels:

For more detailed information about security levels, see your Internet Explorer documentation.
Note ADO and RDS objects will not work in Internet Explorer 4.x with ActiveX controls unless the security level is set to either Medium or Low.
You can customize your security settings in Internet Explorer to allow trusted sites to run ADO and RDS objects while still protecting you computer and data from potentially damaging controls. You can assign sites that you trust to your trusted sites zone, and set the security level to Low or Medium, allowing those applications on those sites to run.
Following are instructions for customizing security behavior in both Internet Explorer 4.x and 5.0.
The following table shows how Internet Explorer 4.x responds when ADO and RDS objects are encountered in different security settings.
| Security zone | Default security level | Respnse to ADO/RDS objects inside Internet Explorer 4.x |
| Local Intranet zone | Medium | When an unsafe operation is attempted, Internet Explorer displays a warning message. You are prompted to either cancel or continue with the operation on your computer. |
| Trusted Sites zone | Low | When an unsafe operation is attempted, Internet Explorer displays a warning message. You are prompted to either cancel or continue with the operation on your computer. |
| Internet Sites zone | Medium | Unsafe operations are not allowed. Internet Explorer prevents the operation. |
| Restricted Sites zone | High | Unsafe operations are not allowed. Internet Explorer prevents the operation. |
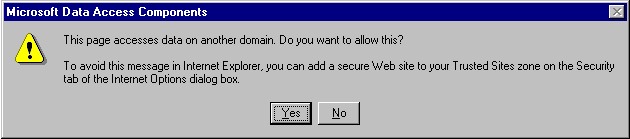
Internet Explorer displays the following dialog box whenever an unsafe operation is attempted:
The default settings listed can be changed. You can change the security level to another level, or you can specify the custom security setting for various actions.
Note By changing the security level, you affect all security related behavior of all objects (including ADO and RDS objects) running in the browser in that particular zone.
Follow these steps to change the default setting for a specific security zone:
If you want to enable unsafe operations and do not want a prompt message box to appear each time such an operation is attempted, you should assign your safe, trusted sites to the Trusted Sites Zone and customize the behavior of the ActiveX controls for that zone. This will enable ActiveX objects from trusted sites to be more functional than all other zones.
To assign trusted sites to the Trusted Sites Zone:
To control the behavior of ADO and RDS objects in a specific zone, you need to create a custom security level and assign it to the zone in which the sites that contain the objects reside. Follow these steps:
When this option is selected and an unsafe operation is attempted, you will see the message, "The page is accessing a data source on another domain. Do you want to allow this?" If you select Yes, the operation is completed. If you select No, the operation is canceled.
Caution By setting Enable for Initialize and script ActiveX controls not marked as safe, you are allowing any ActiveX control to be used from within Web pages. This potentially exposes user computers to malicious controls or malicious scripting code. It is recommended that this be done only in the Intranet or Trusted Sites security zones and not in the Internet zone.
The following illustration shows the security levels and settings in Internet Explorer:
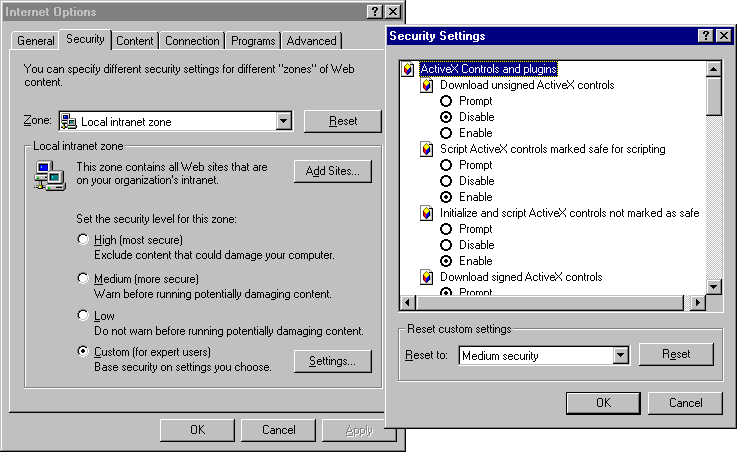
Your ADO and RDS objects will now behave consistently with the specified custom mode. These settings affect the following behavior of ADO and RDS objects in the specified security zone:
There are two exceptions to be considered when running ADO and RDS objects in Internet Explorer 4.x:
For example, for the following code to work inside Internet Explorer, the security setting for Initialize and script ActiveX controls not marked as safe must be set to Enable:
dc.server="http://fred"
dc.SQL="select * from authors"
dc.connect="dsn=books;uid=rU*?;pwd=bcml;"
dc.refresh
rs = dc.recordset
rs.save "c:\mydirectory\myrecordset.xml", adPersistXML
The following table shows how Internet Explorer 5.0 responds when ADO and RDS objects are encountered in different security settings.
Note A Medium-Low security level is introduced in Internet Explorer 5.0.
| Security zone | Default security level | Response to ADO/RDS objects inside Internet Explorer 5.0 |
| Trusted Sites Zone | Low | Unsafe operations are allowed. None of the described restrictions apply in this setting. |
| Local Intranet Zone | Medium-Low | When an unsafe operation is attempted, Internet Explorer displays a warning message. You are prompted to either cancel or continue with the operation on your computer. |
| Internet Sites Zone | Medium | Unsafe operations are not allowed. Internet Explorer prevents the operation. |
| Restricted Sites Zone | High | Unsafe operations are not allowed. Internet Explorer prevents the operation. |
The following illustration shows the security zones in Internet Explorer 5.0:
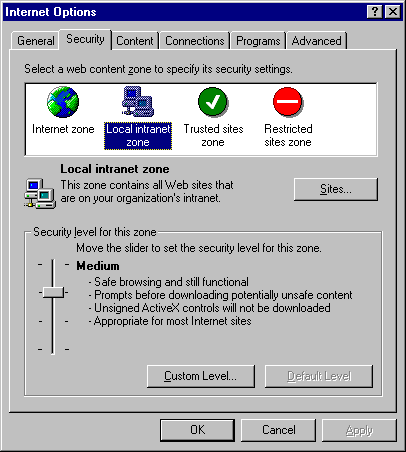
Internet Explorer displays the same dialog box whenever an unsafe operation is attempted as is illustrated in "Internet Explorer 4.x Security Behavior."
You can change default settings by changing the security level or by specifying the Custom security setting for various actions. In Internet Explorer 5.0, the behavior of ADO and RDS objects is controlled by setting the value of the Access data sources across domains option.
When you change the security level, you can also change the behavior of disconnected ADO Recordset objects running in the browser. If you want to enable unsafe operations and do not want a prompt to appear each time such an operation is attempted, you can assign trusted sites to the Trusted Sites Zone.
By using a new option introduced in Internet Explorer 5.0, you can also customize the behavior of ADO and RDS objects by directly customizing the security settings, without affecting how other ActiveX objects behave in that specific zone.
To customize ADO and RDS security settings for a specific security zone, follow these steps using Internet Explorer 5.0:
When this option is selected and an unsafe operation is attempted, you will see the message, "The page is accessing a data source on another domain. Do you want to allow this?" If you select Yes, the operation is completed. If you select No, the operation is canceled.
The following illustration shows the security levels and settings in Internet Explorer 5.0:
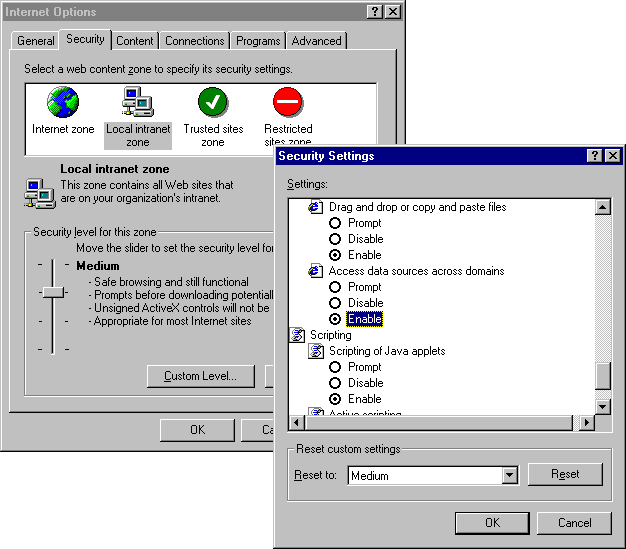
Your ADO and RDS objects will now behave consistently with the specified custom mode. These settings affect the following behavior of ADO and RDS objects in the specified security zone:
Typically, HTML pages are accessed directly from local computers, without going through a Web server, because this is how Web browser applications are designed. When the HTML pages are ready, they are published on a Web server. Pages loaded from a local computer receive special treatment for security considerations. For example, for a page address such as c:\inetpub\wwwroot\msadc (and not a World Wide Web link, http://), unsafe operations are allowed.
In Internet Explorer 4.x, unsafe operations are always allowed on pages loaded from the local computer. Also, in Internet Explorer 5.0, the default is the same for pages loaded from the local computer zone and therefore unsafe operations are allowed. However, in Internet Explorer 5.0, you can change the behavior of the pages loaded from the local computer with the Internet Explorer Administration Kit (IEAK). Refer to your Internet Explorer documentation for more details about the administration kit.
Note If you save a Web page on your local computer, you are giving permission for that particular page to allow data access operations on your computer. In Internet Explorer 5.0, the original address of a page is saved along with the particular page you are viewing. It is not allowed exclusive permissions when saved to the local computer by default.
You can use ADO and RDS to build applications that run in traditional client/server environments or in Internet and intranet environments. When you create an ADO or RDS application hosted in Microsoft Visual Basic®, Microsoft Visual C++®, Microsoft Visual J++™, or an ASP script (on the server side of a distributed application), all operations are allowed because no Internet security restrictions apply.
But when you create an application in which ADO or RDS objects are used in script code running inside a browser, it is important to ensure that these applications do not gain unauthorized access to information and that users of the applications can trust them.
A trusted environment is Internet Explorer in which the user has set the security level to either Medium or High. Because the ADO and RDS objects automatically adhere to security settings, Internet Explorer will alert the user when controls or applications containing these objects are about to run on the user's computer. If the security level has been set to High, Internet Explorer will not allow the control to run.
The following sections, "Safe Objects," "Unsafe Objects," and "Unsafe Operations," describe possible ADO and RDS behaviors in detail.
A safe object is one that will not damage a user's computer or gain unauthorized access to data. The following objects are considered safe to run in a trusted environment:
In the Internet Explorer environment, the developer can directly create and work with these safe objects by using scripting code.
An unsafe object is one that may damage a user's computer or gain unauthorized access to data. When the security level in Internet Explorer is set to High, unsafe objects are not allowed. The following objects are considered unsafe when the security level is set to High:
When the security level is set to High, Internet Explorer will not allow these unsafe objects to be created directly or indirectly on the user's computer.
Unsafe operations are those that could damage a user's computer or gain unauthorized access to data. Internet Explorer is designed to protect a user's computer and data with the security zones and security levels. No code running inside the browser should be able to damage the computer or gain unauthorized access to data on the client computer or any other computer on the same network as the client. For this reason, certain ADO and RDS functions are restricted or not allowed when running inside Internet Explorer. However, if you trust the author of a Web page, you can specifically allow these ADO and RDS functions to run inside that page by customizing the security settings as previously discussed.
In most cases, unsafe operations include those in which an object accessed from a Web page attempts to access data on the local computer, or attempts to access another computer on the local intranet of which the application is not a part. These local two-tier or DCOM connections could allow unauthorized access to data. The ADO and RDS objects are restricted in which connections they can make, and are often only allowed to connect back to the server on which they reside.
When the DataControl object runs inside Internet Explorer, the following restrictions are applied against its operations:
For example, the following connections are not allowed when running inside Internet Explorer using a Medium or High security setting:
' Open a connection to a database on the local computer
dc.server=""
dc.SQL="select * from authors"
dc.connect="dsn=books;uid=rU*?;pwd=bcml;"
dc.refresh
' or...
' Open a connection over DCOM to a remote computer
dc.server="fred"
dc.SQL="select * from authors"
dc.connect="dsn=books;uid=rU*?;pwd=bcml;"
dc.refresh
For example, if the page has been downloaded from a URL that begins with http://server1, then dc.server must be equal to http://server1.
When the DataSpace object runs inside Internet Explorer, the following restrictions are applied against its operations:
' Invoke a business object on another computer within the current domain
set myobjproxy = ds.createobject ("busobj.class", "fred")
' or...
' Invoke a business object on the local computer
set myobjproxy = ds.createobject ("busobj.class", "")
This means that the second parameter in the CreateObject method call on the DataSpace object should point to the same server from which the page has been downloaded.
For example, if the page has been downloaded from a URL that begins with http://server1, the second parameter in the CreateObject method call on the DataSpace object must be equal to http://server1.
When the Connection object runs inside Internet Explorer, the following restrictions are applied against its operations:
"provider= MSDataShape; data provider=MS Remote;Remote server=fred;Remote Provider=sqloledb;database=books;uid=rU*?;pwd=bcml;"
cn.open "provider=ms remote;remote provider=sqloledb;remote server=http://fred;dsn=books;uid=rU*?;pwd=bcml;"
When the Recordset object runs inside Internet Explorer, the following restrictions are applied against its operations:
The connection string must start with either "Provider=MS Remote" or "Provider=MSDataShape".
You can still load a Recordset from the same Internet server from which the page originally came. Therefore, the following code is considered safe if it runs in a page that has been downloaded from a server named "http://fred":
Rs.open "http://fred/recordsets/myrs.xml",,,,adCmdFile
"provider= MSDataShape; data provider=MS Remote;Remote server=fred;Remote Provider=sqloledb;database=books;uid=rU*?;pwd=bcml;"
For example, the following connection is considered safe if the page from which the code is running has been downloaded from a server named "http://fred":
cn.open "provider=ms remote;remote provider=sqloledb;remote server=http://fred;dsn=books;uid=rU*?;pwd=bcml;"
Security behavior in Internet Explorer 4.x environments that is changed in MDAC 2.1 includes:
Note This behavior pertains only to Internet Explorer 4.0.