
The Windows NT directory services domain models
In the NT 4.0 world, there are four accepted domain models: single domain, master domain, multiple master domain, and complete trust. Of the four models, the last represents the least efficient and most complex. Each of the models is designed to create a single user account for each user on the network, but each does this in a different way. We'll take a look at each of these models in more detail.
Single domain model
The single domain model is the simplest to set up and easiest to maintain of all the domain models. It consists of a single NT domain with one primary domain controller (PDC) that houses the master copy of the Security Account Manager (SAM) database. All of the domain's user account information, including passwords, is stored in the SAM. When a network uses this architecture, all network resources, including user accounts, machine accounts, printer queues, and resource shares, retrieve their security principal definitions from the centralized SAM database. User accounts are then granted rights to various resources based on Access Control Entries (ACEs) in the Access Control List (ACL) for whatever resources are being shared or restricted.
In this architecture, there can be only one copy of the SAM database that's modified at any given time, and that copy is owned by the PDC. The PDC then replicates the SAM to any backup domain controllers (BDCs), if necessary.
For small networks, the single domain model is the best choice. Administration is centralized, as are accounts and resources. Single domains are also easy to configure, because there are no trust relationships to configure. See the sidebar, "Establishing a trust relationship between domains," for more information on domain-trust relationships.
Although it may not seem so, the single domain model is also very good for small networks distributed over a wide area network (WAN). Having one PDC in a central location connected to remote BDCs over a WAN connection, such as the Internet, is a very efficient way to centrally administer a corporate network that's spread out over a large area.
Single domains can't be used in all situations, however. Because of software limitations, the SAM can only contain 40,000 accounts, consisting of user accounts, group accounts, and machine accounts. In addition, as single domains grow larger and larger, the hardware required to maintain acceptable PDC performance becomes more and more costly.
Master domain model
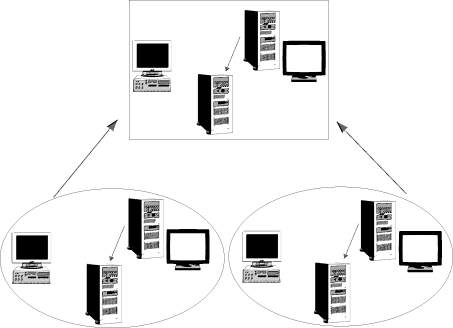
While the single domain model is ideal for situations where you'd like to centralize all network administration, the master domain model allows you to maintain one user accounts database and distribute administration duties for resources. You do this by creating a single master domain, much like the single domain, and then establishing trust relationships with one or more resource domains. Shown in Figure A, the master domain contains all of the user accounts, while the resource domains simply contain resources, such as print and file servers, or NT services, such as SQL and IIS servers.
Figure A: The master domain model is best used for organizations
that want to centrally administer user accounts, but allow individual
departments to administer resources.
This model is ideal when you wish to partition available network resources into separate administration spaces. You can still maintain all user accounts from a single domain controller, while enabling each department, or location, to administer their own resources. Additionally, resources can be grouped into domains either by location or department.
On the down side, the master domain is limited to 40,000 accounts, just as the single domain is. If you have more than 40,000 users, groups, and machines, you won't be able to use this model. Further, you'll have to establish a one-way trust relationship for each resource domain on the network. Finally, even as the number of accounts approaches the 40,000 limit, performance begins to decrease, if the PDC hardware isn't sufficient. For enterprises that have close to that number of users, the only real choice is the multiple master domain model, which we'll discuss next.
Multiple master domain model
The multiple master, or multi-master, domain model is the only real choice for networks with over 40,000 users. It's also the best model to be used in organizations that have divided administration resources. In this model, shown in Figure B, two or more master domains contain all of the user accounts. All master domains establish two-way trusts with all other master domains. Under each master domain, a number of resource domains contain the resources, as in the master domain model. Not only must each resource domain establish a trust relationship with its master domain, but also with the master domains of any users who may need to access their resources. The secondary trust relationships are indicated by the dotted lines shown in Figure B.
Figure B: The multi-master domain is right for networks with
more than 40,000 users.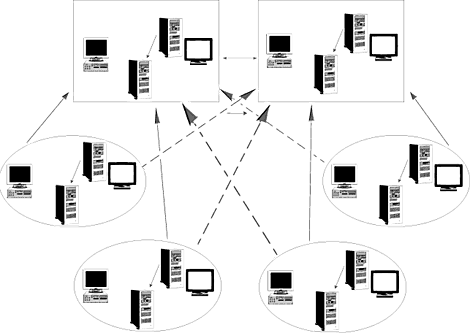
While allowing more users than the single master domain, the multi-master domain model retains some of the advantages of the simpler model. Administration of user accounts is still centralized and administration of network resources is still decentralized.
Unfortunately, the multi-master domain model is the most complex and requires the most forethought. Users' accounts are distributed over multiple servers, and multiple trusts must be established. Furthermore, you must create global groups in each of the master domains, if the standard groups don't meet your needs. While the work required to create and maintain a multi-master domain may seem extreme, in the long run this model is more efficient than the complete trust model. We'll take a look at that next.
Complete trust domain model
The last domain model, and it really isn't much of a model, is the complete trust architecture. This model, shown in Figure C, is typically found in organizations that haven't planned for network growth. Each domain in this model contains its own user accounts and resources, thereby making all administration decentralized. This design should be avoided if at all possible, as it's the most costly in terms of network resources.
Figure C: The complete trust model is the least efficient domain
architecture.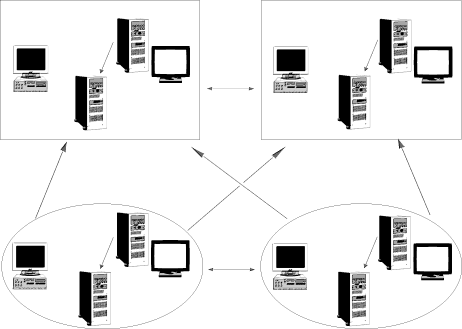
In this model, all domains are established as master domains and each domain must establish a two-way trust relationship. To calculate the number of trusts a network would require, you can simply multiply the number of domains by the number of domains less one (D * (D - 1)). As you can see, the more master domains you add, the more trust relationships you'll need to create.
Conclusion
Every organization has different needs and requirements for their network. Using one of the three recommended domain models will help you develop a domain architecture that will help your network grow. Deciding which model is right for your network can be difficult, but the rewards are well worth it. To help you decide, Table A contains a brief recap of the advantages and detriments of each model. As you plan a new network or learn more about how your existing network is designed, understanding the various domain models will help you avoid problems and may help you troubleshoot problems for an existing network. Next month, we'll look at what Windows 2000 and the Active Directory provide to make domain planning and implementation easier.
Table A: The four domain models
| Domain Model
|
Main advantage
|
Main disadvantages |
| Single domain | Easy to set up and maintain. | Can't have more than 40,000 users. |
| Master domain | Allows for decentralized administration of resources. | Can't have more than 40,000 users. |
| Multi-master domain | Allows more than 40,000 users | Complex to set up and administer. |
| Complete trust | Requires little or no planning. | Very difficult to administer. |
Copyright © 1999, ZD
Inc. All rights reserved. ZD Journals and the ZD Journals logo are trademarks of ZD
Inc. Reproduction in whole or in part in any form or medium without
express written permission of ZD Inc. is prohibited. All other product
names and logos are trademarks or registered trademarks of their
respective owners.